5-Step Plan for Enhancing Information Management & Privacy Act Compliance

News & Insights
Privacy on Purpose 5-Step Plan for Enhancing Information Management and Privacy Act Compliance
Why Privacy Matters
In an increasingly digital world, New Zealanders rightfully expect their personal information to be treated with care, respect, and transparency. From schools and councils to private businesses and not-for-profits, every organisation that handles personal data has a legal – and moral – obligation to uphold the principles of the Privacy Act 2020. Beyond compliance, safeguarding privacy builds trust. Whether you’re responding to access requests, managing sensitive employee data, or using digital tools like Microsoft 365, OneDrive and Teams, how you handle information speaks volumes about your values.
But privacy doesn’t manage itself. It takes deliberate action, embedded processes, and an organisation-wide culture of responsibility.
This 5-Step Plan for Enhancing Information Management and Privacy Act Compliance is designed to help your organisation go beyond box-ticking. It blends practical guidance with trusted local resources – like the Office of the Privacy Commissioner’s e-learning tools and response calculators – to help you build systems that support both compliance and care.
Let’s get started.
5-Step Plan
- Establish Awareness and Responsibility: Educate staff on privacy responsibilities and define roles
- Develop Integrated Policies: Create policies addressing privacy principles and management best practices
- Implement Information Systems: Optimise digital tools for better information management
- Embed Compliant Processes: Set up accessible processes for handling complaints and breaches
- Continually Monitor and Improve: Regularly review practices and stay updated on legislation
Establish Awareness and Responsibility
Educate all staff on their privacy responsibilities using resources like the Privacy Commission's free e-learning tools. These cover topics from Privacy 101 to reporting privacy breaches.
Clearly define roles and responsibilities for information management and privacy compliance, including the role of Privacy Officers.
Consider conducting initial Privacy Impact Assessments (PIAs) to identify potential privacy risks associated with current information handling practices.
Develop and Implement Integrated Policies and Procedures
Create comprehensive internal policies and procedures that address both the 13 Privacy Principles and broader information management best practices (drawing on areas like digital workplace strategy, record keeping, and content management).
Establish clear processes for handling access and correction requests, keeping in mind the Response Date Calculator from the Office of the Privacy Commissioner.
Develop a robust data breach response plan, outlining the steps for identification, containment, assessment, notification and review.
Implement and Optimise Information Management Systems and Practices
Review and optimise your organisation’s use of digital workplace tools (e.g., Microsoft 365, SharePoint, Teams) to improve information organisation, accessibility,
and security. Consider solutions that help solve content problems and reduce information silos.
Establish clear guidelines for document management, record keeping, and information retention, aligning with both legal requirements (including the Privacy Act
and the Public Records Act, if applicable) and organisational needs.
Embed Complaint Handling and Breach Management Processes
Establish a clear and accessible process for individuals to lodge privacy complaints directly with your organisation first. Follow the guidance in Handling privacy complaints: a step-by-step guide.
Ensure your data breach response plan is well understood and regularly tested. Have clear protocols for determining if a breach is notifiable to the Privacy Commissioner and affected individuals.
Personal Information Management and Privacy Compliance Framework
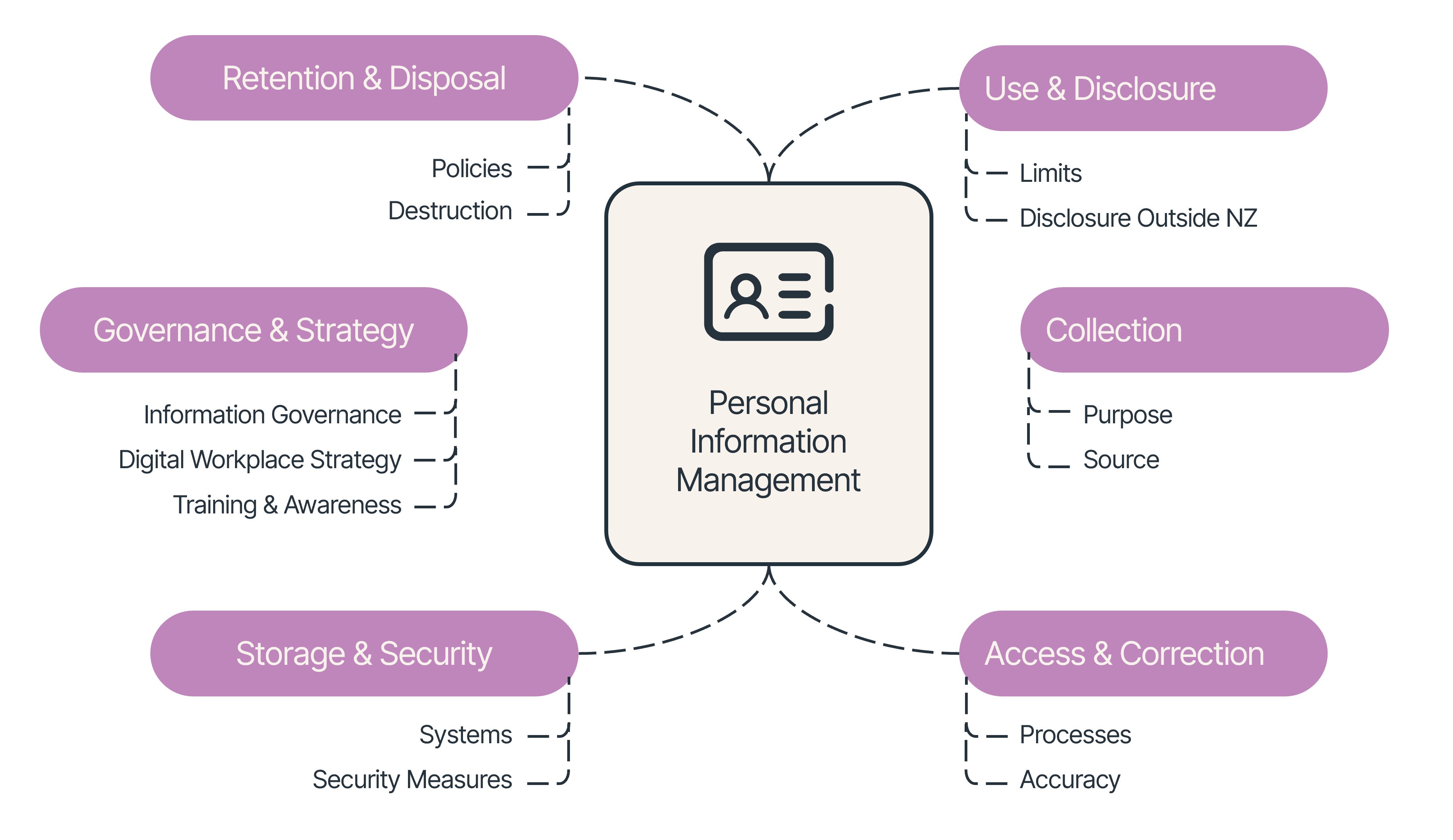
Top Tips
- Don't need it, dispose of it: Regularly review and dispose of unnecessary content to keep your workspace organised and boost security and compliance.
- Implement access controls: Implement strong access controls to protect sensitive information and ensure only authorised personnel can access, modify, or delete data.
- Classify with purpose: Use sensitivity labels to classify and protect your content, ensuring sensitive information is handled securely.
- Education reduces risks: Educate employees on content retention and disposal to reduce risks of breaches and noncompliance.
- Data privacy policies: Document your data privacy policies to ensure legal compliance and maintain stakeholder trust.
.svg)


